User Groups
The concept of user groups is very easy to understand. Instead of treating users individually, they can be grouped together and treated as one single entity. A user can be part of multiple groups but it is up to the administrator to decide which groups he belongs to.
Suppose an organization wants to group users by region, like this:
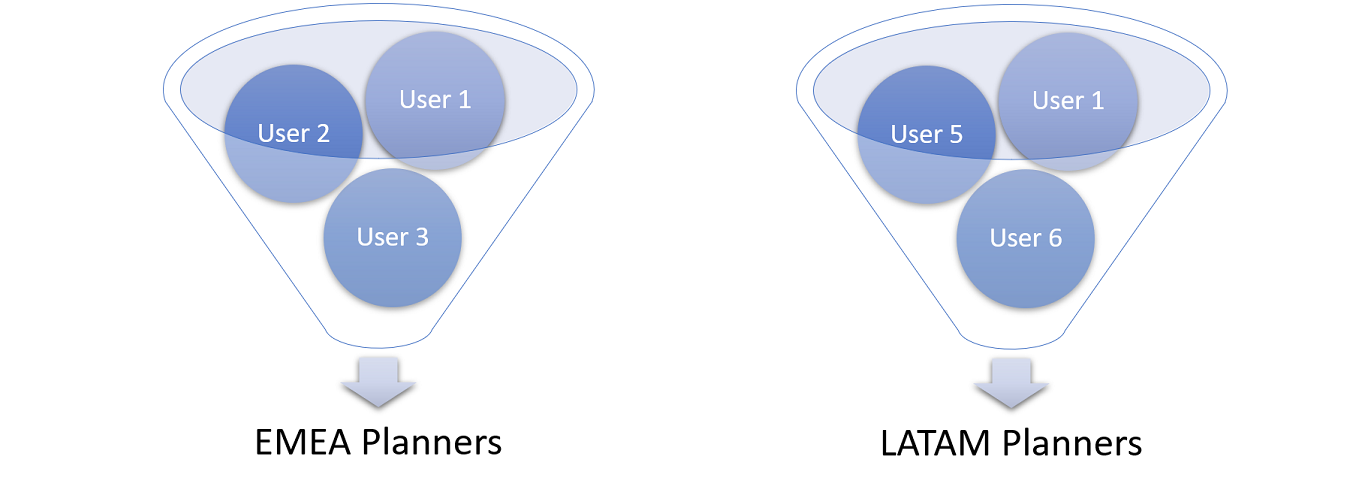
Users in a group usually share common traits and also probably need the same kind of privileges and data.
Instead of assigning filter values, categories and time markers to the users one by one, user groups can be used. When a user is assigned to a user group, the specifications for that group will automatically be allocated to the user. These allocations can be accumulated as well. In the example above, "User 1" is part of both groups, which means that this particular user will be able to do everything users from group 1 and group 2 can do, which for instance could be to plan tasks and resources in both EMEA and LATAM regions.
Sharing data
As you know by now, profiles and layouts can be shared. There are currently two sharing options: it can be shared with everybody (public) or it can be shared with a user group.
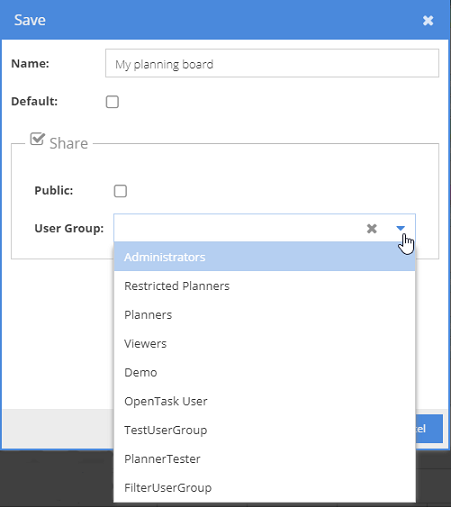
Everybody who is a member of a group will have access to the profiles and layouts that were shared with that group. When a user is removed from a group, he will no longer have access to these privileges.
Security
Roles
Treating similar users through user groups makes it easier to manage security, as roles can be assigned to user groups. Everybody who is a member of a group is granted the user actions that were assigned to that user group. As soon as he is removed from a group, the user will no longer have access to these privileges. Naturally, when the user was assigned directly to a role (or through another user group), he may not see any difference at all.
Data-driven security
There is also data protected security through the assignment of filter values, categories and time markers to user groups, which are then compared to tasks and resources. For more information about data-driven security, click here.